Greetings to my fellow Cybernites, today we are going to discuss about the only thing which I am good at, which is GOOGLE HACKING AKA DORKING.
The contents on the topic will be as followed:
- Definition
- History
- Advance operators
- Protection
Definition:
“Google Dorking", also known as “Google Hacking”, is a technique used by newsrooms, investigative organizations, security auditors as well as tech savvy criminals to query various search engines for information hidden on public websites and vulnerabilities exposed by public servers. Dorking is a way of using search engines to their full capacity to penetrate web-based services to depths that are not necessarily visible at first.
All you need to carry out a Google Dork is a computer, an internet connection and knowledge of the appropriate search syntax.
History:
Google Dorking has been in existence from the early 20th century, unlike other successful hacks, Google Dorking is world-weary. It simply requires you to use certain special keywords sometimes creatively by a supported search engines. Talking about Dorking it is impossible to forget the great messiah of Dorking Johnny Lang aka j0hnny hax.
In an 2011 interview, Johnny Long said, “In the years I’ve spent as a professional hacker, I’ve learned that the simplest approach is usually the best. As hackers, we tend to get down into the weeds, focusing on technology, not realizing there may be non-technical methods at our disposal that work as well or better than their high-tech counterparts. I always kept an eye out for the simplest solution to advanced challenges.”
Rather than an ordinary type of search query that focuses on a semantic way of asking questions, either directly through writing the whole question or selected key words, google Dorking is based on reverse engineering the way machines scan and index web content.
Advance Operators:
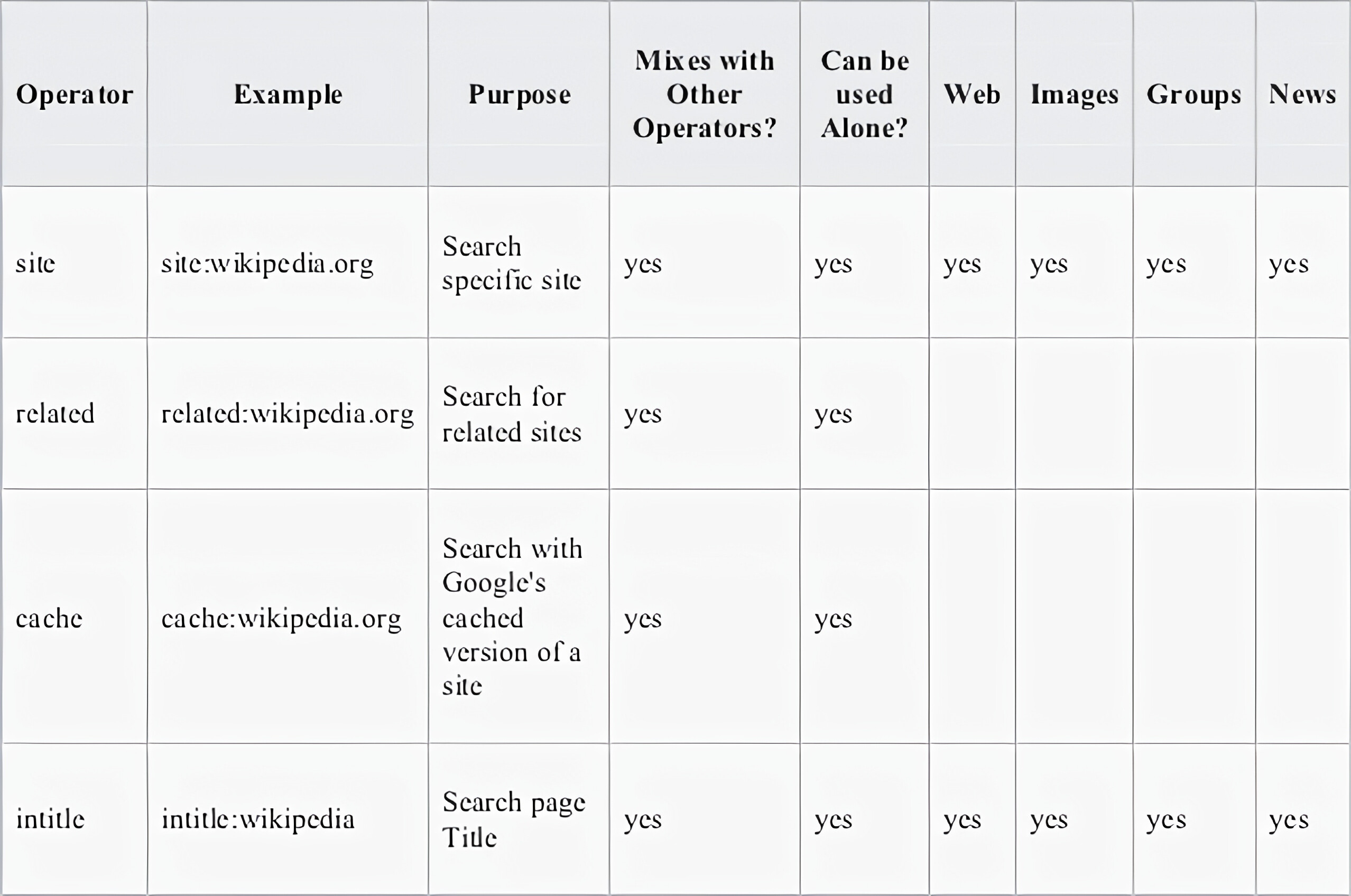
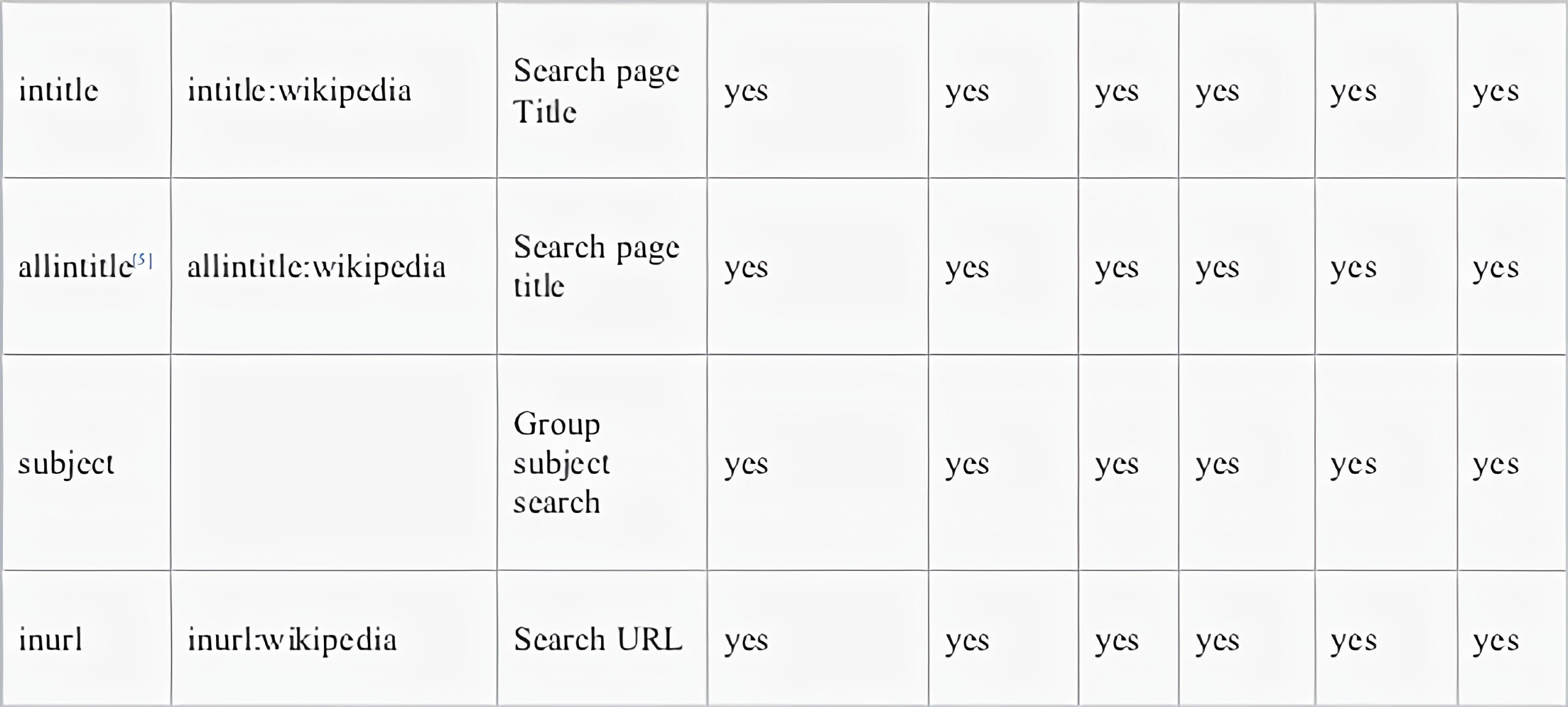
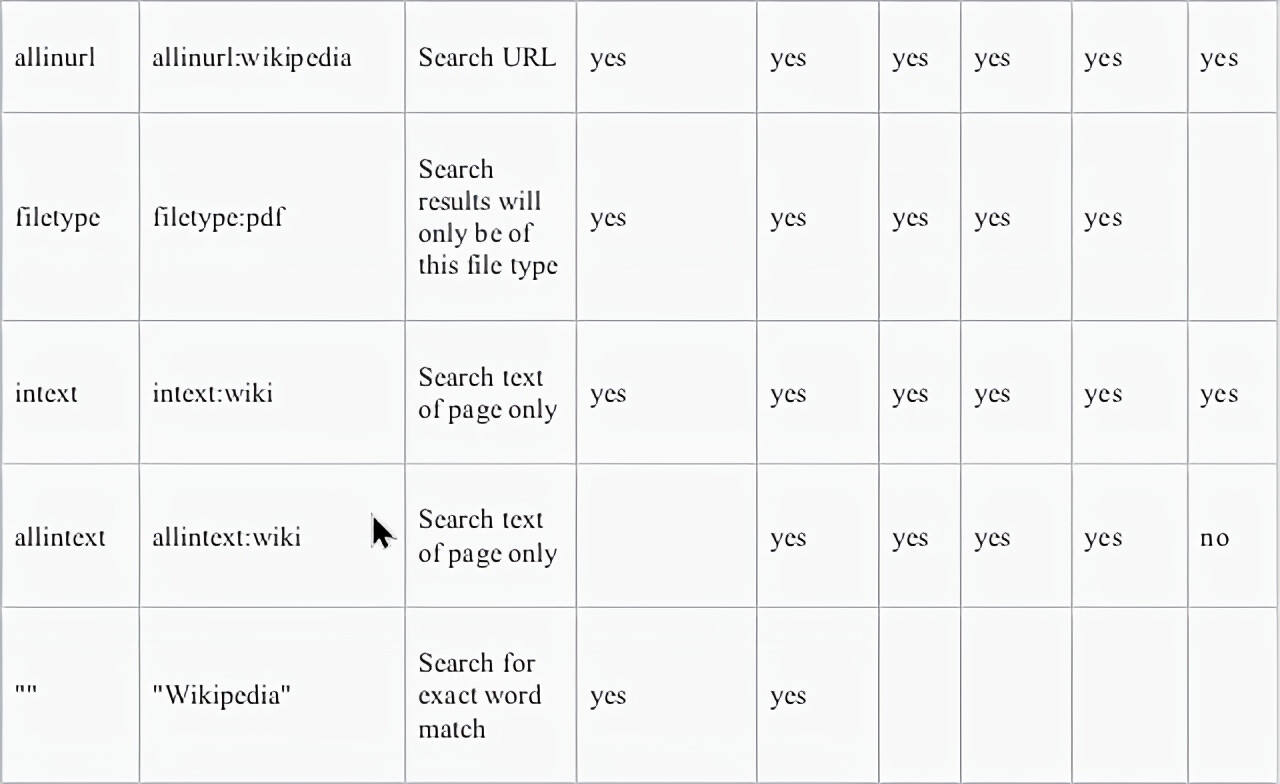
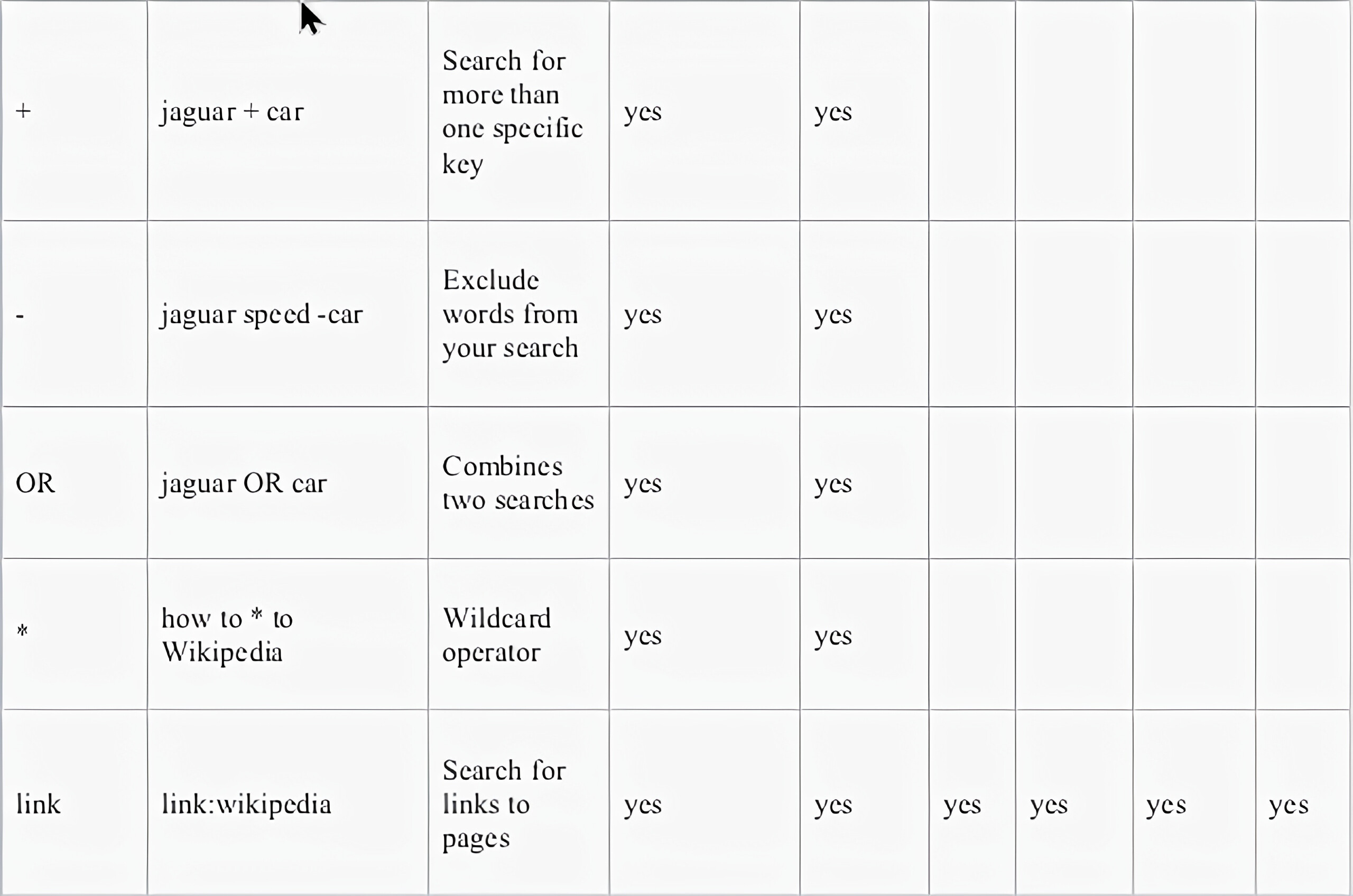
Advance operators are basically a type of specific keywords which helps you at optimizing google Dorking searches.
Thanks to Wikipedia I don’t have to make this table. Bless my lazy soul;)
Many similar advanced operators can be used to exploit insecure websites:

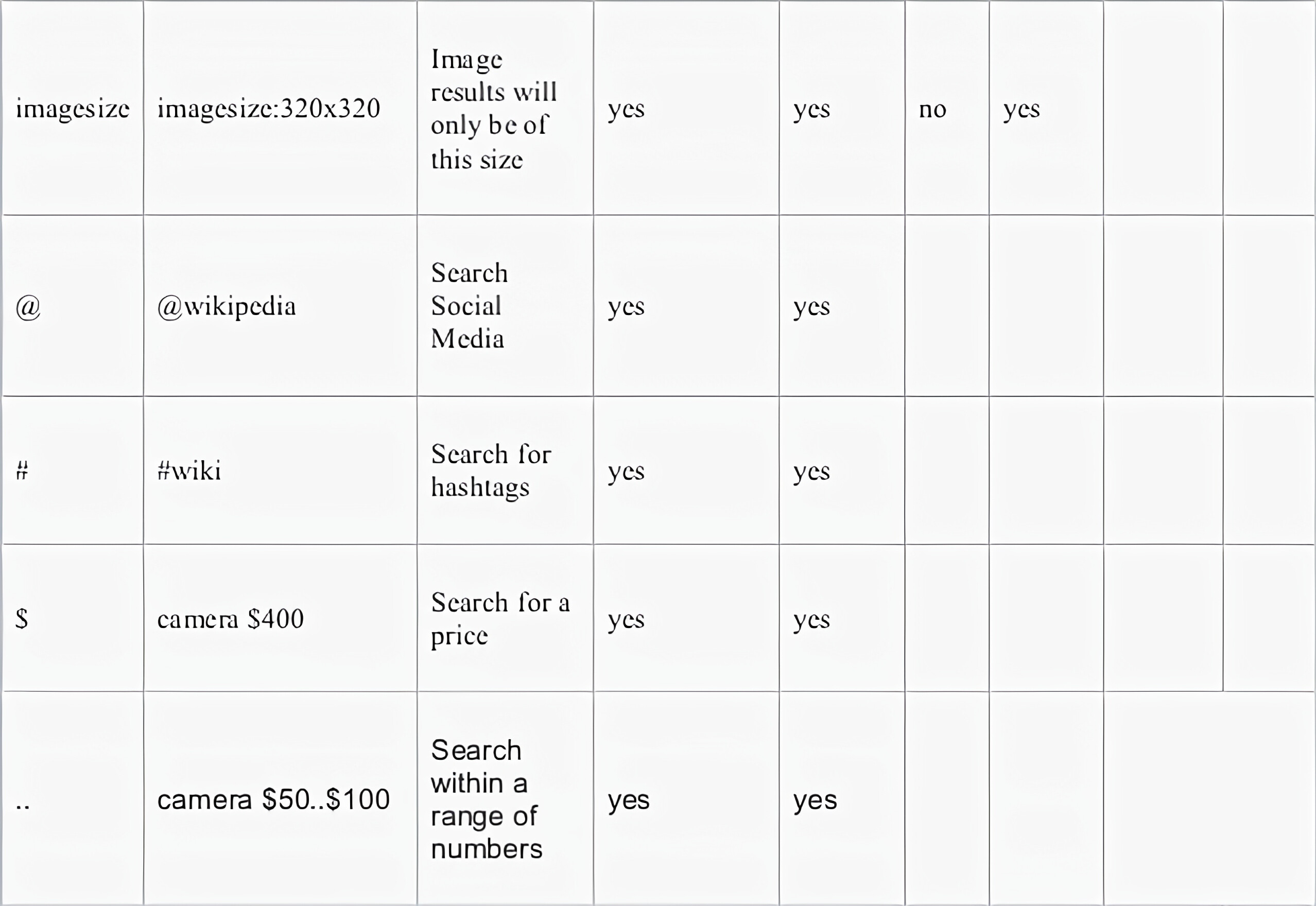
Protection:
There are a great deal of approaches to abstain from falling under the control of a Google Dork. These measures proposed include:
- Encoding/encrypting sensitive data such as usernames, passwords, payment details, messages, addresses, telephone numbers, and so forth.
- Run inquiries against your own site to check whether you can locate any sensitive data. On the off chance that you discover sensitive information, you can remove it from search results by utilizing Google Search Console.
- Protect sensitive content by utilizing a robots.txt document situated in your root-level site catalog. Utilizing robots.txt helps prevent Google from indexing our site, but it can also show an attacker where sensitive data might be located.
So where do we start? The accompanying arrangement will deny all creeping from any registry inside your site, which is truly valuable for private access sites that don’t depend on freely indexable Internet content.
User-agent: *
Disallow: /
You can also block specific directories to be excepted from web crawling. If you have an /admin area and you need to protect it, just place this code inside:
This will also protect all the sub-directories inside.
User-agent: *
Disallow: /admin/
Restrict access to specific files:
User-agent: *
Disallow: /privatearea/file.html
Restrict access to dynamic URLs that contain ? symbol:
User-agent: *
Disallow: /*?
~ Constantine AKA Dorker 