
MACHINE :
A machine is a thing that is created by people to make work easier. It is a tool or invention which multiplies the effect of human effort.

DEVICE :
A device is a unit of physical hardware or equipment that provides one or more computing functions within a computer system. It can provide input to the computer, accept output or both.
DATA :
Data is a collection of facts, such as numbers, words, measurements, observations or just descriptions of things.

COMPUTER :
A computer is a machine that accepts data as input, processes that data using programs, and outputs the processed data as information. Many computers can store and retrieve information using hard drives. Computers can be connected together to form networks, allowing connected computers to communicate with each other.

NETWORK :
A network is a collection of computers, servers, mainframes, network devices, peripherals, or other devices connected to one another to allow the sharing of data. An example of a network is the Internet, which connects millions of people all over the world.

INTERNET :
The Internet, sometimes called simply “the Net,” is a worldwide system of computer networks – a network of networks in which users at any one computer can, if they have permission, get information from any other computer.

PROGRAM :
A computer program is a collection of instructions that can be executed by a computer to perform a specific task. A computer program is usually written by a computer programmer in a programming language. PROGRAMMING LANGUAGE :
A programming language is a formal language comprising a set of instructions that produce various kinds of output. Programming languages are used in computer programming to implement algorithms.
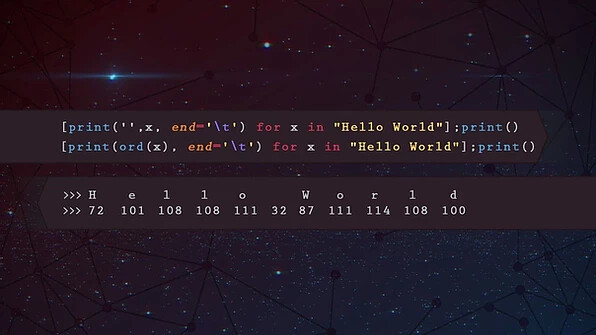
HACKING :
Hacking is an attempt to exploit a computer system or a private network inside a computer. Simply put, it is the unauthorized access to or control over computer network security systems for some illicit purpose.
The term ‘Hacker’ was coined in the 1960s at the Massachusetts Institute of Technology to describe experts who used their skills to re-develop mainframe systems, increasing their efficiency and allowing them to multi-task.

ETHICAL HACKING :
Ethical Hacking is an authorized practice of bypassing system security to identify potential data breaches and threats in a network. The company that owns the system or network allows Cyber Security engineers to perform such activities in order to test the system’s defenses. Thus, unlike malicious hacking, this process is planned, approved, and more importantly, legal.
Computer security, cyber security or information technology security (IT security) is the protection of computer systems and networks from the theft of or damage to their hardware, software, or electronic data, as well as from the disruption or misdirection of the services they provide.

Yeah, if in-case you are thinking that, why are we telling these so silly explanations, then u might want to change your point of view… Yeah, these all are inter-connected. Well, OK, anyway we are not gonna keep you guys just with these but these are the small and first steps to lead into our full-time ETHICAL HACKING The At Most BASIC into The At Most ADVANCED!!
Stay tuned with us…!